April 28, 2016
Get Your KICS en Route to Industrial Protection.
Hurray!
We’ve launched our KICS (Kaspersky Industrial CyberSecurity), the special cyber-inoculation against cyber-disease, which protect factories, power plants, hospitals, airports, hotels, warehouses, your favorite deli, and thousands of other types of enterprises that use industrial control systems (ICS). Or, put another way, since it’s rare for an enterprise today to manage without such systems, we’ve just launched a cyber-solution for millions of large, medium and small production and service businesses all around the world!
So what’s this KICS all about exactly? What’s it for? First, rewind…
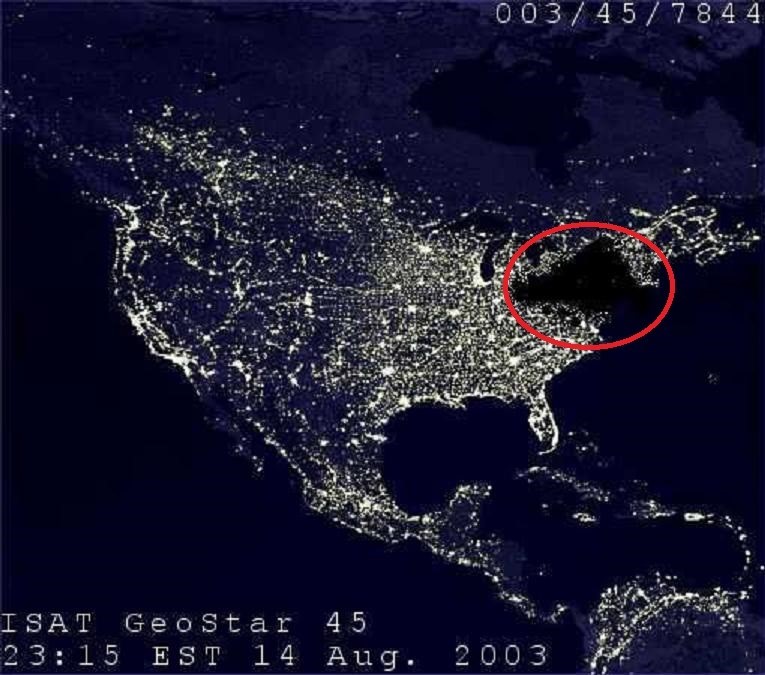
Before the 2000s a cyberattack on an industrial installation was a mere source of inspiration for science fiction writers. But on August 14, 2003 in northeastern USA and southeastern Canada, the science fiction became a reality:
Because of certain power grid glitches, 50 million North Americans went without electricity – some for several hours, others for several days. Many reasons were put forward as to the reasons behind this man-made catastrophe, including unkempt trees, a bolt of lightning, malicious squirrels, and… a side-effect from a cyberattack using the Slammer (Blaster) computer worm.
As far as I understand, what actually happened was a combination of all these factors. I mean, there was a freak occurrence (trees/squirrels) and at the same time the worm accidentally brought down the communications system: a small-scale, localized emergency turned into a large-scale, regional one because the central-level control mechanisms weren’t able to deal with the situation, causing it to domino to cover the whole region.
Incidents such as these probably occurred before, since both ICS and computer networks have been around for several decades. But those incidents were either hushed up or put down to other causes. What’s more important today is the fact that ever since 2003 there’ve been more and more news stories about cyberattacks on industrial objects, and they’re gaining in frequency. And in 2010, the Stuxnet attack on the Iranian nuclear program showed that the issue has a military aspect.
Conclusion: Industrial facilities are also vulnerable to cyberattacks; what’s more, the consequences of ignoring this fact can be ohhhhhh so unpleasant – sometimes even catastrophic.
All righty. It’s clear industrial installations need protecting. But how?
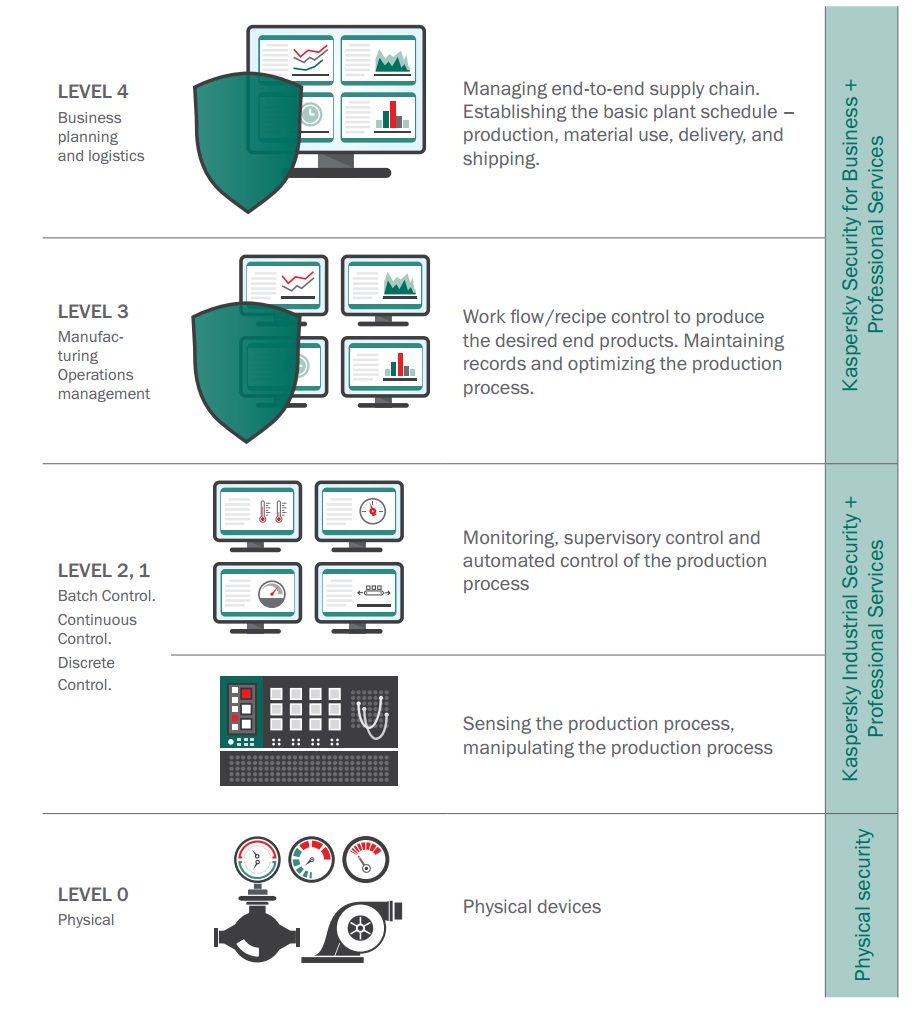
Well, the bog-standard endpoint solutions – they protect only part of the infrastructure of enterprises – specifically, the bit that’s normally called the corporate network. Protection of production processes – the industrial network – requires a completely different approach since industrial networks are a whole different kettle of fish – from the things being protected (PLC, SCADA, HMI…), to the environment they’re in, and most importantly their functions and how they fulfill them.
Unlike with the regular office IT environment, what’s crucial for the industrial IT environment controlling production processes is uninterrupted, continuous – 24/7 – operation: that’s what’s most important of all. So much so that the classic trinity of key concepts of information security – confidentiality, integrity, and availability (in that specific order) – are reordered for industrial networks to become availability, integrity, and confidentiality. But to be secure, well, we can’t be having that customized threesome now can we?! So that’s why we KICked ourselves into action to come up with KICS.
Let’s be clear from the outset: this isn’t a product; it’s a solution.
Simply installing security software doesn’t protect an industrial network. Instead, internal processes, technologies and equipment need to be analyzed; a model of threats and a protection strategy need to be developed; software needs adapting to the specific requirements of the network; specialists need training; and a lot more besides – and all of it to maintain the all-important continuity.
We did all that – helped by consulting with corporate/industrial customers and analyzing best practices – and already have two successful implementations of KICS – one at an oil company, the other at a seaport. And the initial results in both have been reeeaaally interesting…
…Unfortunately, as can be expected, I can’t tell you all the details. I can only provide an overall picture, so at least you can get some idea of what we’re up against:
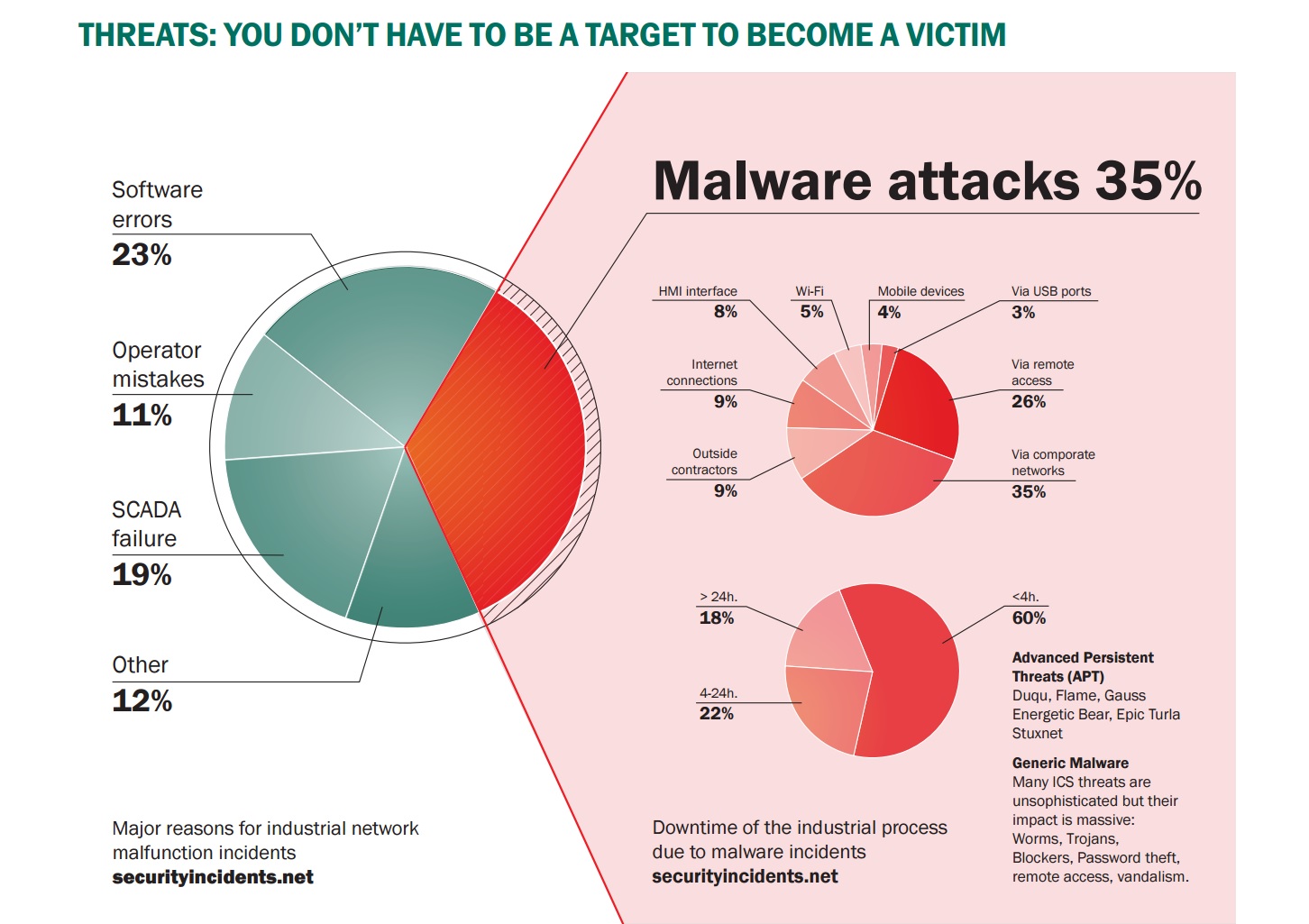
Within just a few days of KICS’s operation on one customer’s industrial network we uncovered not just one but several serious security violations, including the unsanctioned connection of a laptop by an employee (oops!). Like I say, that was within just a few days. Can you imagine what we’ll find in a month, a year? Yep – all sorts of hazards; but that’s what KICS is for: to protect against all of them.
In some respects industrial networks are even less protected than the standard corporate IT environment. Really!
There’s a popularly held viewpoint in the world with regard to industrial objects that states that ‘if it works, don’t touch it’; of course, not everywhere, but such a dictum does, alas, predominate. What that means is that if a computerized production process works smoothly, it may never have updates installed on it for 20+ years! It may get connected to the Internet… – no matter! Main thing – JUST LEAVE IT BE! And woe behold anyone who might get fancy ideas about improving security: they’d be out the door before they could utter: “Patching? This century? Guys? HELLO?” if they halted the process for just a single minute.
But we can’t be having whole industrial control systems left vulnerable in this day and age just because they demand continuity. We just can’t.
Late last year we held and open cyber-contest for studying attack vectors against critical infrastructure. We used for the contest a stand with a real electrical substation on it – built according to modern technologies and standard IEC1850.
And guess what happened?
It was hacked within three hours – not just with one attack method, but two. And over the full two days it was hacked 26 times, with many of those hacks bringing the substation to a complete standstill. All devices on it were completely wrecked, and even a zero-day vulnerability was discovered on it!
But have no fear – KICS is here! It caught out every single attack. That is, on a real network it would have prevented them all – and yes, dear production-line engineers, without halting production for a second!