February 3, 2012
DDoS – a Nasty SOB, but Curable – with KDP.
Hi everyone!
The Russian parliamentary elections late last year and the ensuing mass protests against their alleged falsification have brought about a sharp increase in the level of polarization of viewpoints being bandied about on Russian-language social networks and online media.
Simultaneously with all this, plenty of the Russian online media were visited by a ghost – the ghost of DDoS (Distributed Denial of Service Attack) – in early December 2011. This led to brazen hacker attacks, with one after another Russian website going down, and several attacks occurring simultaneously. Some were organized using traditional criminal bot networks, but behind them, it sure seems to me, stood marginal political groups, since the victims of the attacks were the sites both of opposition groups (including the Communist Party) and also of the ruling United Russia party.
A second DDoS attack – in mid-December – was more sophisticated. To date we still don’t have any reliable information about its origin – that is, not technically (how they actually pulled off the DDoS), and not the people who ordered it. And I’m not sure we’ll ever get to the bottom of it.
But I won’t get bogged down here with theory.
Let me get straight to DDoS in action.
First, let me tell you a bit about how we monitor botnets and fight DDoS, and also about our super-duper cure-all pill – our anti-DDoS solution called KDP (Kaspersky DDoS Prevention – currently available on the Russian market only, but we’re testing the ground here).
Most DDoS and KDP descriptions you can find on the Internet are rather complicated and really just for experts. Here, I’ll translate that geek-fest into understandable, accessible language. Hopefully after reading this you will have a basic idea of what DDoS really is. And this really is quite useful to have – so as not to get all panicky the next time the press gets the fundamentals about DDoS all mixed up; oh, and also to realize who the good guys are (yes – that’s us at KL :)
So, let’s start from the beginning. What is DDoS?
Well, the principle underlying DDoS doesn’t apply only to the world of computers and networks. It applies to all sorts of things (particularly to young families with at least three children – they’ll know what I’m talking about (it’ll become clear soon…)); it even applies to hot dog stands!
Example: let’s take a hot dog stand plus one hot dog-server – let’s call him Bertrand – at a train station at a sea port. Bertrand can serve three customers per minute. A train comes into the station near to where the stand is situated and 20 passengers all at once would like to get some hot dogs (no, they can’t wait for their proper food at home). A line forms. People have to wait a while for their guilty pleasure, but still, the hot dog stand is working and the product’s getting sold (and Bertrand’s working up a sweat).
Then a boat arrives at the port – handily for this example, right by the hot dog stand – and a further 100 hungry souls join the line. This lot must have had a choppy ride since they all together get hot and bothered about having to wait. This then boils over into direct-action protest – they start pushing and shoving Bertrand and then rocking the hot dog stand to and fro as if this might secure them quicker service. Of course, instead of service speeding up, it grinds to a halt, and all the respectable folk from the train who had been waiting patiently in line and not carrying on like the spoilt-brat-like boat travelers end up without hot dogs (as of course do the dim-wits from the boat).

(с) palimphread // flickr
Well, it’s kinda the same situation with websites. When too many require “service” (for example, to read the news from voting stations), at first the servicing system gets slowed down; then, with ever increasing requests, the same thing happens as in the example: a sharp decline in output and eventually a full-on jam. The essence of DDoS attacks is the deliberate emulation of such service requests (a “flood”) – the creation of a huge line (of boat-trippers who don’t really want hot dogs – they’re just pretending), so that regular users (train travelers) can’t get their portion of content (hot dogs).
So how does this emulation work?
Generally speaking, as you may have already guessed, many different computers send a site their communications requests. Usually the requests come from botnets – big networks made up of computers infected with special malware. These botnet computers receive a command to target a particular site from their control center, and these botnet computers – unbeknown to their owners – start to flood the victim. How many requests a site can cope with depends on how powerful its equipment is and its bandwidth. For those who want to know more – go here.
It stands to reason that when a large part of our life has moved online, big business and big politics will also have made the move. Especially when one considers that DDoS has proved to be a reliable tool for smothering a competitor, blackmailing an online service, or generally giving a hard time to anyone, etc. (see our statistics). At the same time, accompanying ills have also appeared – like blaming everything under the sun (in terms of security breaches) on DDoS; this is only logical – since hardly anyone knows what it is. And if someone reasonably objects that it’s not all down to DDoS – they get condemned for being an enemy of democracy or an agent of the Kremlin/Washington/Tel-Aviv/Tbilisi… Classic!
How can you protect yourself from DDoS?
The simplest way is to have humungous bandwidth plus 12-cylinder, six-liter equipment (I remember my Countach stats :). That way botnets have a tough time flooding a site. One problem with this though is that it’s crazy expensive, so not always a viable option. There are plenty of other measures – and half measures. For example, black-holing (blocking attacking traffic together with normal traffic – not a viable option for businesses); having different IDS/IPS systems (ineffective against overloading the band); or site settings optimization (works only against weak attacks).
The KDP idea isn’t new, but this method of protection from DDoS is today the most effective. The idea is as follows. A KDP system takes over the traffic of an attacked site, shuffles it all about and puts it into dozens of geographically far-flung and very obese reserve bandwidth, and then filters the traffic with different analysis technologies (signature, behavioral, statistical, etc.). After all this putting-through-the-meat-grinder, KDP returns cleaned traffic to the site. And Bertrand can start selling his poison-in-a-bun again.
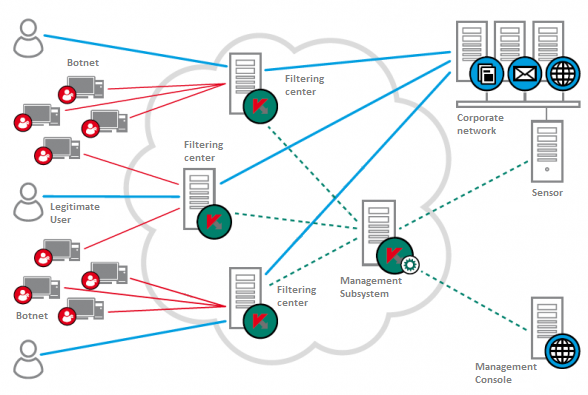
In essence, what KDP does is provide temporary rental of some very powerful bandwidth + a filter. What’s more, the switching occurs quickly – to get an attacked site back up is possible within a couple of hours, with clients receiving notification about anomalies practically in real time. The effectiveness of the cleaning-up of parasitic traffic is from 98% (UDP/SYN/ICMP/TCP Connect Flood) to 80% (DNS-attack). Our Clients? We have several dozen, but I’m afraid I can’t tell you who they are – non-disclosure agreements prevent me from doing that. I can say that they are made up of government organizations, banks, the media… – all sorts of different clients.
KDP would be just another banal anti-DDoS thingy (of which there are plenty), if not for one circumstance. As you know, what we do is protect against malware. And the cyber-wretches have for years already been monetizing malware via botnets – the same botnets via which the vast majority of DDoSs come from. So we know our DDoSs – inside-out. And what we do is disembowel all this malware, dissect the methods of attack, and continuously train KDP to fight it the best way.
A collateral product of analysis is the data we glean from monitoring the activity of botnets and seeing who attacks and when, and whom and how. Oh course, there aren’t the resources to monitor all the botnets in existence, but we keep our close eye on plenty. Besides, we exchange information with our competitors (and they – us), so it’s really simple to establish whether a site was really attacked or whether it was just some attempt at PR.
A completely logical objection can arise here: “So, KL knows all about botnets, but instead of closing them down, makes money out of them!” Just hold your horses. We do shut them down – aplenty. And if only you knew how much of a long and disagreeable task it is – hampered by: providers, which don’t want to lose their slice of the (traffic) pie; obstinate (corrupt?) bureaucracy; technical difficulties; and many other factors. So we move forward slowly, but surely.
Here is an example – our work with the Dutch police against the Bredolab and Shadow botnets and our recent cooperation with Microsoft in taking down Hlux/Kelihos.
So there you have it, in a nutshell – the basics about DDoS and the methods we use in fighting it.
And to all victims of the December and in fact any DDoSs, there is one thing I suggest…
DDoSs represent a problem that needs solving. To do nothing but moan and point the finger at Kremlin/State Department/… scheming – this is some kind of small-minded and just plain daft delirium. That is, of course, if a DDoS attack actually took place at all and it’s not just a good excuse for covering some spectacular security fails and other cock-ups.

