June 30, 2014
Cybernews from the dark side: June 30, 2014
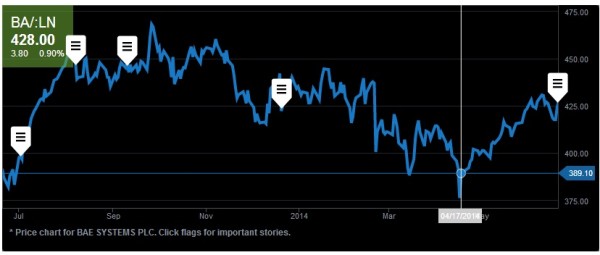
Stock market hacks for microsecond delays.
Cyber-swindling gets everywhere. Even the stock market. First, a bit of history…
The profession of stockbroker was once not only respected and honorable, but also extremely tough. Dealers in stocks and shares once toiled away on the packed floors of stock exchanges and worked silly hours a week, stressed to the limit by relentless high pressure decisions all day (and night). They bought and sold securities, stocks, bonds, derivatives, or whatever they’re called, always needing to do so at just the right moment while riding the waves of exchange rates and prices, all the while edging nearer and nearer to serious heart conditions or some other burn-out caused illness. Other times they simply jumped out of windows to bring a swift end to it all. In short – hardly the world’s best job.
Anyway, all that was long ago. All that hard manual labor has been replaced by automation. Now thinking hard, stressing and sweating aren’t needed: a large proportion of the work today is carried out by robots – special programs that automatically determine the very best moments to buy or sell. In other words, the profession of stockbroker has in large part been boiled down to the training of bots. And to these bots reaction times – to the microsecond – are vital to take advantage of this or that market swing. So speed literally depends on the quality of an Internet connection to the electronic stock exchange. That is, the nearer a robot is physically located to the exchange, the higher its chances of being the first with a bid. And vice versa – robots on the periphery will always be outsiders, just as will those not using the very latest progressive algorithms.
These critical reaction times were recently tampered with by unknown cyber-assailants. A hedge fund’s system was infected with malware to delay trading ability by a few hundred microseconds – which can – and probably did – make all the difference between clinching deals and losing them.
Your password for a Twix?
Perhaps inspired by the pseudo-research conducted on the streets of London some years ago, which found that 45% (!) of women surveyed were willing to divulge their email password for a bar of chocolate, some Americans decided to find out how seducible computer users are when hard currency was on offer.
It turned out that around half of those taking part in the survey were ready to launch an unknown file from an unknown source – for one cent! For 50 cents the level rose to 58%. And for a dollar those who violated one of the principle rules of computer hygiene jumped to 64%!
Just what is wrong with people?
It’s true that computer hygiene is sadly lacking in general, despite the years we’ve put into telling folks the basics. But at the same time, that figure for the password for chocolate – I just don’t believe it!
Let’s have a closer look here: did anyone check whether the passwords given up were actually genuine? Maybe it was all a lot simpler: the female Londoners simply pulled a fast one in order to get the Snickers? That sounds more plausible :).
Half of users are willing to download an unknown file from and unknown source for one centTweet
So, pinch of salt at the ready, palm steadied and readied for the face… let’s just not forget about lies, damned lies, and statistics.
I’ve repeated countless times that there’s no such thing as absolutely secure software – especially so for such complex things like OS. Regarding vulnerabilities, it’s never a question of whether they exist or not, it’s just a question of when they’ll come to light – sooner or later.
Also, there’s a direct link between the popularity of software and its holey-ness – a non-linear one. Why would cyber-villains sweat it by targeting the relatively niche Mac OS, when hundreds of millions of vulnerable Windows comps are at the ready for immediate hire for a botnet? And the more vulnerable Windows comps there are – the less attractive to the underground become other platforms which aren’t as popular. But that doesn’t do away with the rule to be vigilant.
Here’s a fresh example from the world of Linux.
Infrequently – but regularly – we get a whiff of malware for this OS. And normally it’s quite advanced, as Linux programming is mostly done by serious professionals. For example, we recently published this analysis of a family of Trojans for Linux – real heavyweight Trojans able to carry out a DDoS attack with DNS amplification. It was found to be real effective with very limited resources and could even have a good go at bringing the Internet down!
While over in the Apple orchard, notwithstanding occasional mess-ups, iOS is still holding up in terms of security. Thanks to its to secure architecture and pre-moderation of apps malware still hasn’t appeared for iOS (I do hope we haven’t missed anything).
Nonetheless, Apple still needs to be prepared, and to be 100% open and honest with users – happy owners of iDevices who are subject to all sorts of cross-platform attacks, including MITM and phishing. For example, at the current levels of mobile banking apps’ security, even if you’re using an iPhone you should only bank online in really secure locations. Let me tell you more…
…But some are more dangerous than others.
Let’s say you want to check the balance of your bank account using an iApplication in the departure area of an airport. And what do you see after passport control? ‘Free Wi-Fi’! And since spends on 3G add up over time and can get real slow at times – and you’d best check the balance while still at the airport as you’re not going to get stung by those extortionate roaming rates again – you decide it won’t harm to quickly use this free Wi-Fi.
What happens? All your traffic is intercepted by the guys in hoodies in the corner with the laptops…
You have to ask yourself: how well is your connection with the bank encrypted (if it’s encrypted at all)? And might there be some old bugs for which fixes haven’t been released yet? Wanna find out in such a risky way? Yes, it is a rhetorical question.
Still about Wi-Fi…
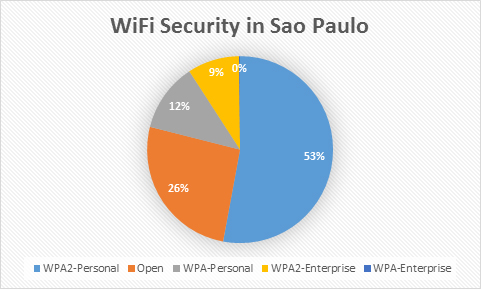
With the World Cup in full swing in Brazil, some of our top researchers decided to check out Wi-Fi access points in and around Sao Paulo, which will be used lots by football fans from all over the world.
How safe is it to use such Internet access and what should be looked out for – have a read here.
And I’m sure that the conclusions in that report are more or less applicable to just about any country – not just Brazil. So, going back to iOS still being secure but also still being vulnerable – just remember: don’t put blind faith in your iDevices’ impermeability: instead – use your head. That rhymes. KL Marketing slogan writers – take note! :)
Spam – still out there.
It’s been a while since I’ve mentioned spam. Maybe our filters are just working so well that we’ve stopped noticing this phenomenon?
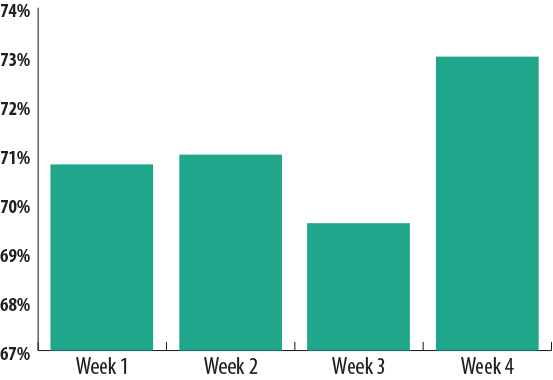
It is true that in recent years spam protection has gotten super slick and the level of spam has been brought down; however, the phenomenon has remained and still in considerable quantities. For example, the share of the pink processed meat in email traffic still makes up around 70%.
And let’s not forget that spam is often used as the delivery mechanism for malware and phishing – especially in reaction to certain news stories and seasonal occasions. To better understand how and why this ecosystem is still going fairly strong – I recommend this here big research into the economics of the pink slime.
Though email spam is being coped with fairly well (I, for one, rarely see it in by inbox), there’s still its younger cousin – telephone cold-calling spam – which is still a serious headache in many parts of the world – particularly on the American continent.
The Federal Trade Commission even decided to ask participants of the upcoming DEF CON hacker conference for help in solving this problem! I’ve always said asking hackers to do your bidding ain’t the right way to go about thing, but still – it shows how desperate some folks are getting. Btw, this is already the second FTA attempt. The first time even a prize of $50,000 brought zero results.
That’s enough cybernews for today folks. See you!…