November 16, 2011
Rooting out Rootkits.
As you might guess from the title, today we’ll be talking about rootkits. At heart this is an interesting topic, but often that ‘heart’ is out of sight: in the press rootkits are rarely covered at all, and if they are the articles are filled with nothing but horror stories that have nothing in common with reality. There are of course many technical articles, but these don’t help the wider audience – the general public.
But the problem exists.
The majority of anti-virus software is making great strides towards protection from rootkits. But this isn’t necessarily a good thing, since not all of it does it properly. The ability to fight them first depends on, and is indicative of, the technological progressiveness and overall level of anti-malware expertise of the developer. And not all ‘developers’ are technologically progressive – so their so-called anti-rookit technologies aren’t up to scratch, leaving overall protection against rootkits around the world lower than it could and should be. And let’s not forget that many botnets use rootkit technologies, and the ability to draw out this contagion is the best protection there is from cybercriminals.
So let’s go through all the salient points about rootkits in order.
We’ll start with the basics. What’s a rootkit?
First off, it’s not an extra-nasty form of malware, though it’s described as such in many a pop-article. A rootkit is simply technology designed to conceal the presence of software on a system – sadly normally malware. This camouflage is used to hide things like malware seizing system functions, changing access rights, locking files, manipulation of kernel objects and much more.
Interestingly, rootkits are not all bad/malicious. The degree of “badness” or “goodness” of a rootkit depends entirely on its author’s intentions. A bit like a kitchen knife – everything depends on how it’s used. It can be a useful home utensil for chopping vegetables, or it can be a lethal weapon. Some positive uses of rootkits are for example (at least for various media-producing industries) copyright protection systems (though it’s best not to keep such rootkits secret from users – as early on Sony BMG found out the hard way), and also emulators of different devices.
Despite the ‘good’ applications, it’s turned out that the general public has come to view this technology as a bad thing. A lot of malware (in fact, the most sophisticated and dangerous) indeed uses rootkits to hide itself from both the user and security software. For example, Stuxnet, TDSS, Sinowal and Rustock. The list goes on, and it’s very long.
For the history, classification and other technical details of rootkits, have a look at the Wikipedia page on them. I’d also recommend this overview article on the evolution of the technology. And let me take off from there.
Rootkits represent really dangerous technology. Several of them have even learned how to get around such elaborate systems of protection like Patch Guard and digitally signed drivers. I’ve no doubt that, to cyberscum, specialists in this field are worth their weight in gold. But it’s quite clear that there are very few true rootkit ‘specialists’ or rootkit ‘authorities’ out there. For example, McAfee’s superbly PR’ed Shady RAT incident (behind which it was assumed stood a nation state) was deemed (not by me!) a crowning achievement in malware technology – but in fact it wasn’t even a rootkit!
Of course, to fight rootkits is not all together that simple. From the standpoint of integration in the operating system and the ability to control internal processes, rootkits are on an equal footing with anti-virus software! As a consequence, deleting rootkits, in particular disinfecting an infected computer, is no trivial task.
The confrontation takes place on three fronts – (i) detection of rootkit modules (prevention of infection); (ii) anti-virus self-defense (so that rootkits don’t take the anti-virus out of the memory); and (iii) full-frontal attack (exploitation of the rootkit’s imperfections to neutralize and delete it).
The most unpleasant thing about rootkits is that now many anti-viruses in the fight against them confine themselves exclusively to detection. They simply add a checksum signature to the database, and in doing so permit detecting a rootkit only in an inactive state. At best they release a stand-alone utility for healing rootkits (as with the latest version of Norton). But what if the computer was already infected before the signature arrived? That’s right – up the creek without a paddle.
To detect with signatures, or, worse, to nick the detection from a neighbor via a multi-scanner, is no difficult feat requiring big brains. But to analyze sophisticated code, improve heuristics, develop generic detection on the whole rootkit family, intercept the malicious script, shut down the vulnerabilities in third-party software, and develop effective treatment – for this one needs both mega brains and mega expertise. For the cyberbaddies can be quite crafty – they can tweak a rootkit ever so slightly so it becomes undetectable by AV of inferior quality, while it opens up an entry point into your computer and allows the active infection to remain.
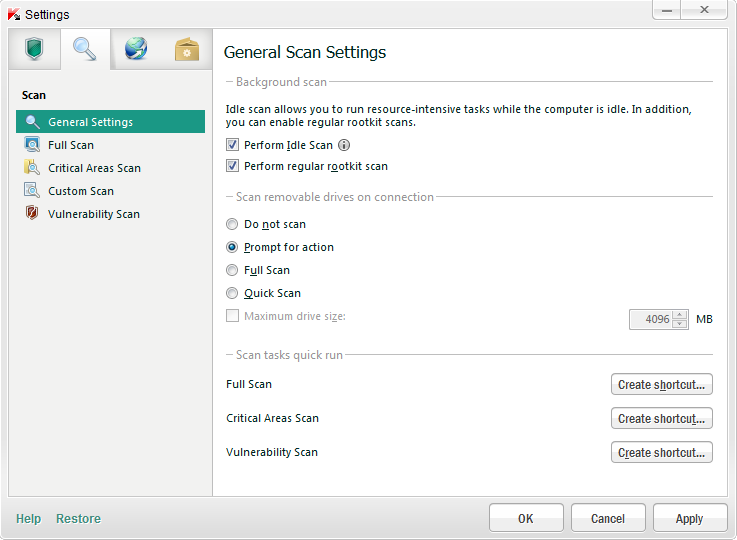
Recently the Anti-Malware.ru test center published the results of a very interesting test that illustrated the ability of different products to treat active rootkit infections. First, my congrats to our AMR (Anti-Malware Research) team. Keep up the great work! I’m very proud of the result, as well as with the progress compared with last year. Second, it’s easy to work out from the results who really carries out investigations, and who prefers to stick with checksum signatures to indulge different irrelevant tests. Third, the test and its results are a good excuse to say a few words about our anti-rootkit technology.
We have two of our own developed tools against rootkits.
The first is QScan – a universal pill against rootkits. The second is MARK – tailored for specific rootkits and their methods of camouflage. If QScan doesn’t cope with something, MARK comes running to its assistance, which conducts deep analysis in the memory and then returns the ‘patient’ back to QScan. Both technologies have loads of neat tricks up their sleeves. For example, QScan is able to get round a rootkit’s trick of disguising its files. QScan analyses the system registry files and assembles files sector-by-sector. I won’t go into any more detail – it gets way too complex. And then of course there would be all the know-how I’d be giving away (!), which is waiting in line patiently in the patent offices of different countries. The main thing though is the result: our products ahead of everyone on protection against rootkits!
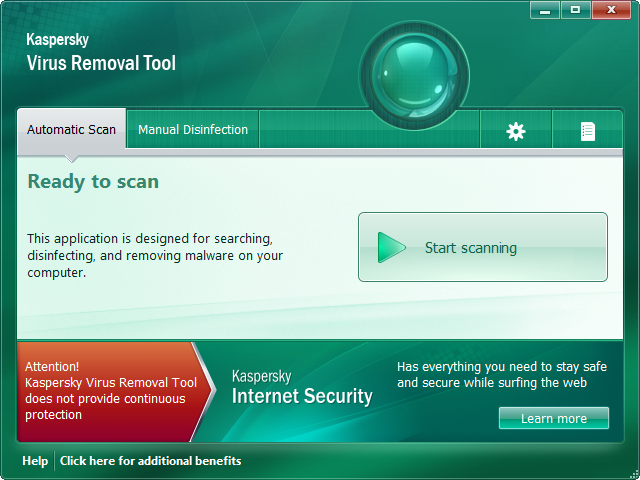
We came up with MARK in 2008. QScan appeared a year later. Since then we’ve been constantly bettering them. Both technologies are part of our anti-malware engine and are present in our commercial (both consumer and corporate) products and free stand-alone utilities (for example the Virus Removal Tool).
I think that as time passes the more sophisticated rootkits will get and the wider their application will be. Already we see old rootkits easily available for purchase on the black market for a few hundred dollars, which can be bolted easily onto malware. In the meantime the technology is evolving in parallel with the operating system. Rootkits have started to support 64-bit Windows (but no worries – we can catch them there too!), even despite the fact that in x64 versions they’ve improved the protection against various system intercepts and modifications. Plus the cyber-miscreants are already using bootkits (also being widely used by legit software), and BIOS-kits are already on the agenda.
IMHO, not to properly develop and progress in this field of malware – as do the majority of anti-virus companies – is wrong, short-sighted, and disrespectful to users. They get a false feeling of security: a Trojan can live ok and get along just fine on a computer ostensibly protected by a so-called effective anti-virus solution, and steal everything. Who needs that?
So just be careful with what you install on your computer.