May 16, 2025
Our updated Sandbox (ver. 3.0): “The Matrix for Malware”.
Something important has happened – though you might have missed it…
The third version of our Research Sandbox has been released!
Hmm. Hardly jaw-dropping, right? But it still matters – big time. Let me tell you why…
What is it?
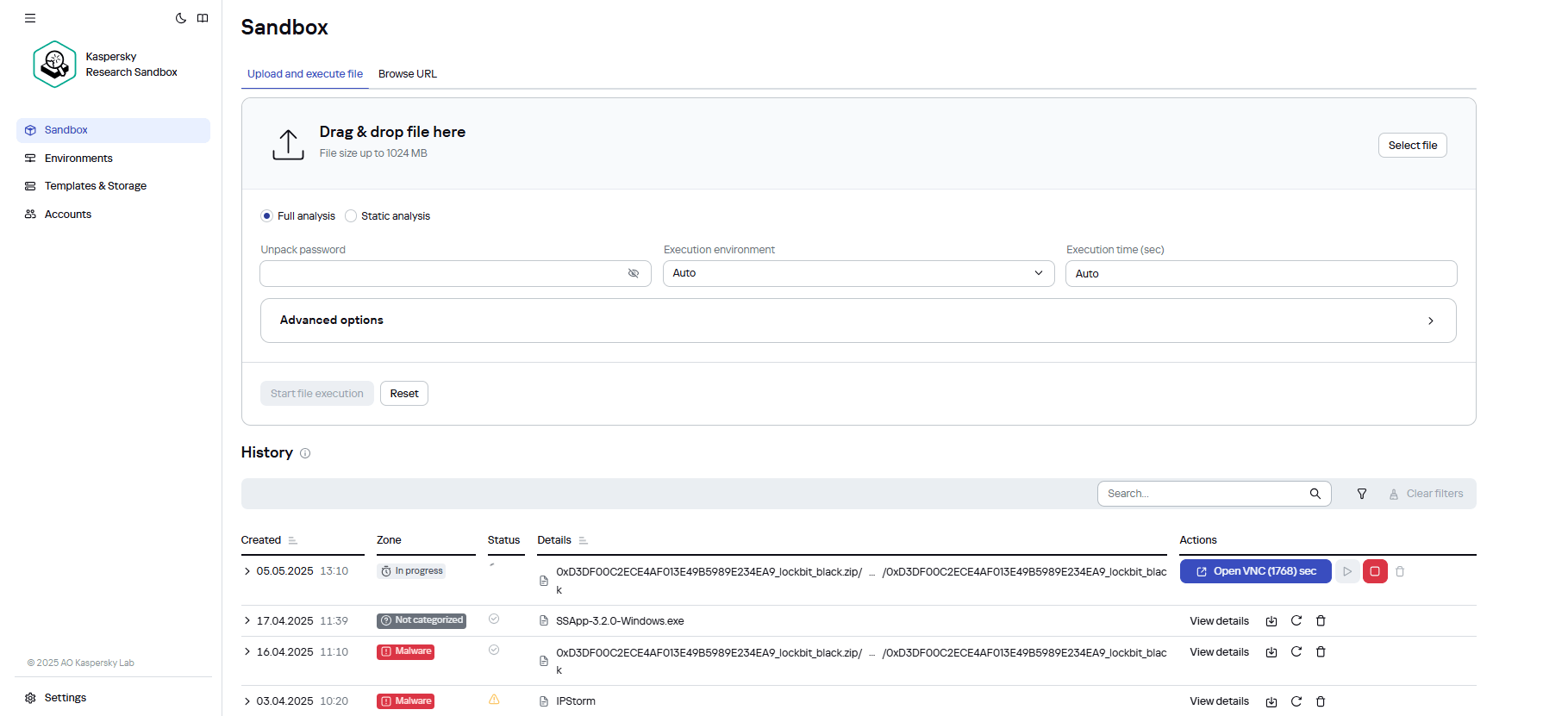
What’s a sandbox? Let me start with the very basics…
How can you tell if an object (file, web resource…) is malicious? The simplest way is to run it and see what happens. If it steals passwords and card data or encrypts files and demands a ransom – there you go: it’s malicious. But “sucking it and seeing” is hardly a great idea given the damage such infections/encryption can wreak.
To safely test a suspicious object in a controlled environment, we created a sandbox – a sort of virtual petri dish where malware can reveal its true malicious colors while we observe it under a microscope.
Static and dynamic analysis
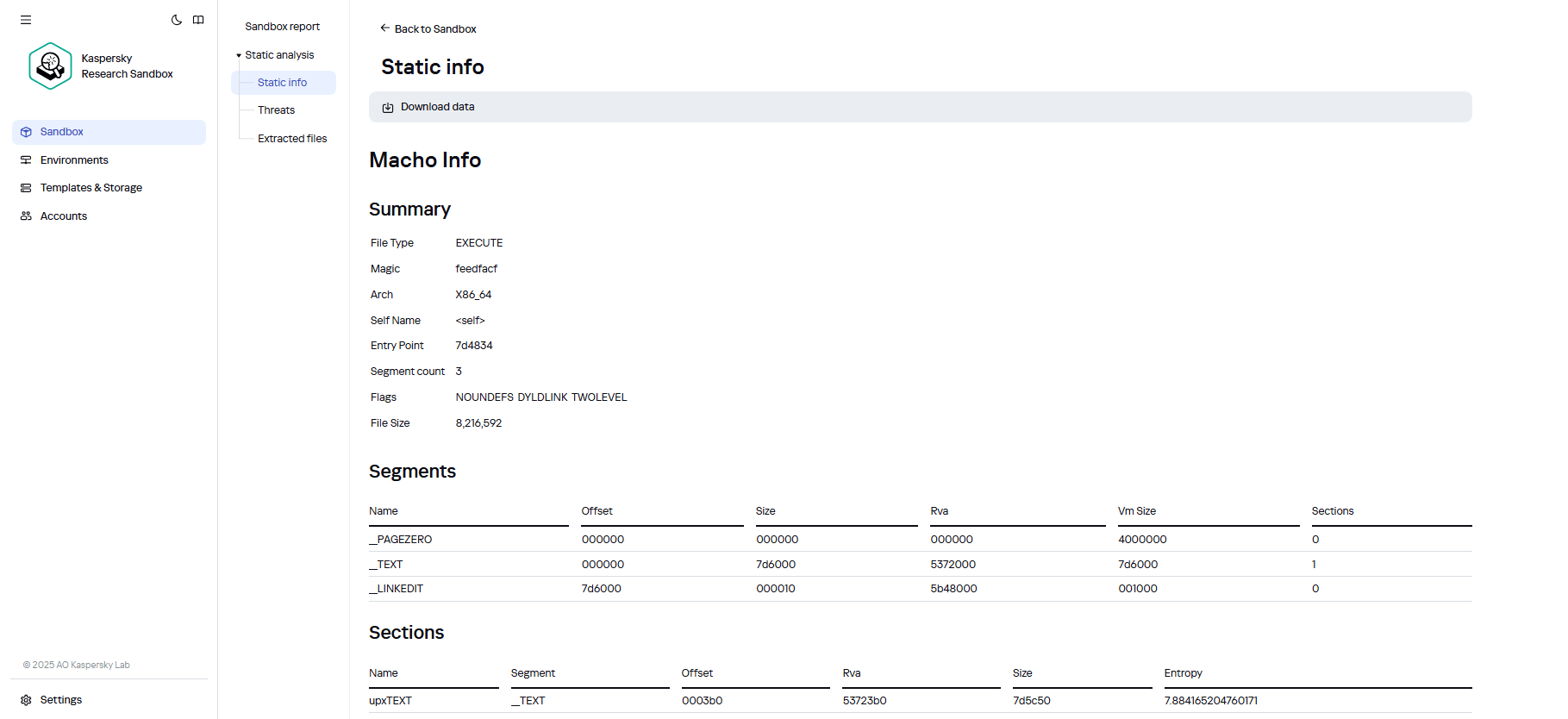
Now for some details on how we analyze an object in the Sandbox. First, it can perform static analysis – disassembling the object, looking at what’s inside, identifying connections, analyzing the file structure, and comparing all this against our reputation-database information and detection rules; searching for known threats, and identifying potentially suspicious features, etc.
Now for the dynamic analysis…
The Research Sandbox can act as a “Matrix” (yes – the one with Neo and Morpheus, not the kinds used in printing or math) for the object – a world where it can live its “normal life”. From the perspective of the running file (script, webpage), the Sandbox appears to be a regular workstation.
Meanwhile, the bad guys are getting forever smarter. They’re constantly getting better at identifying artificial environments and then tricking them.
But back to our Sandbox being like a “Matrix for malware”…
We’ve got cutting-edge technology like a robust event-logging system, and it’s all deeply embedded within the virtual OS and virtualization system layers that malware can’t access. And yes, a real-world workstation environment is also simulated. Files open and close, processes start and stop, the user browses documents, and shops for a robot vacuum on a marketplace, and complains about low pay in a messenger (just kidding, any details on how it works can be provided upon request).
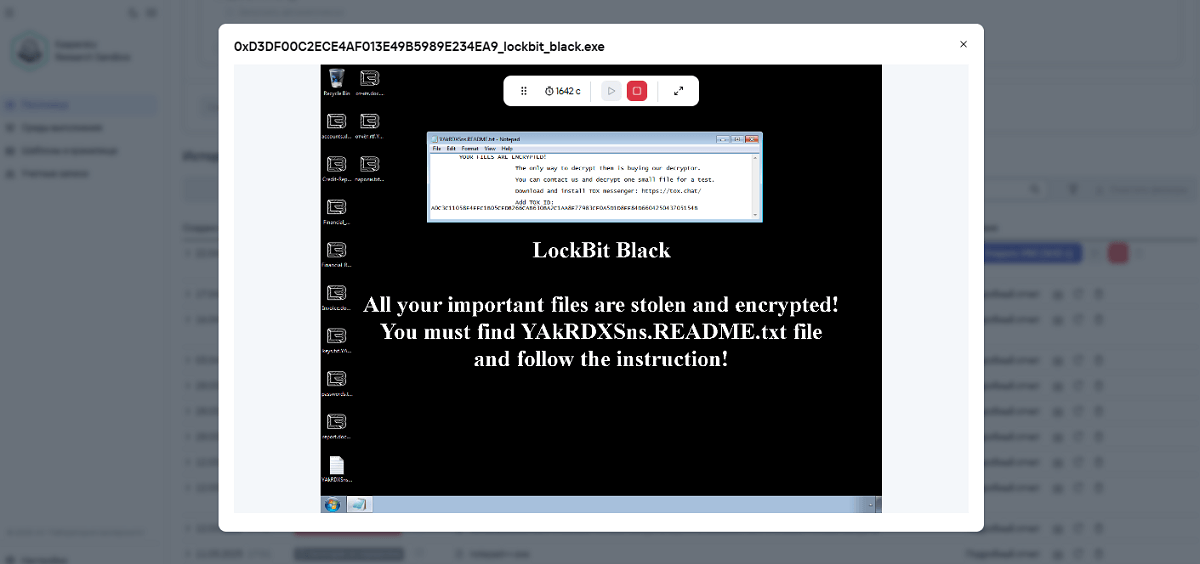
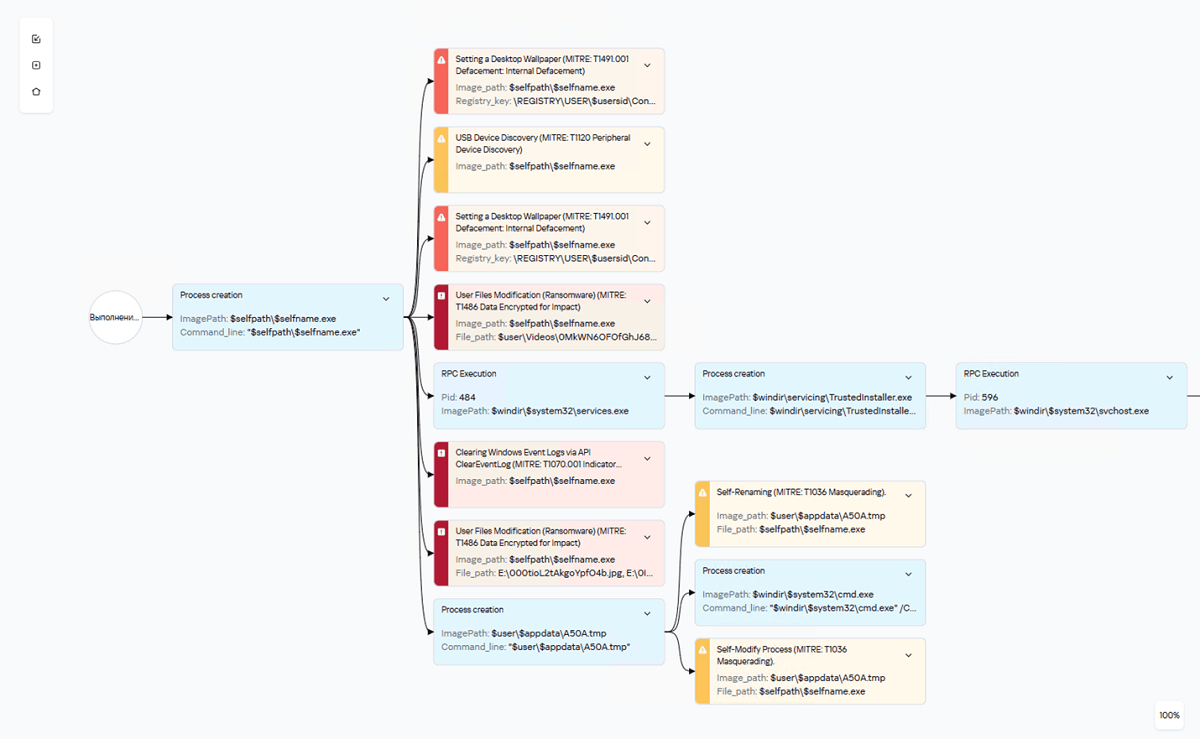
In other words, the file (or webpage or script, etc.) runs, and the analyst watches what happens. In our new 3.0 version, the file that’s running can be observed literally – there’s a special visual mode called VNC. For example, if the malware changes the desktop wallpaper to something threatening (“Pay up!”) or obscene (use your imagination!), you can check out the malicious creators’ handiwork up close. And you can also see how file extensions change as they get encrypted. It’s like an interactive disaster movie for the cybersecurity team – with all the details and full immersion. And I write “interactive” as, not only can the malware be observed in action, but the environment can be tweaked as needed: change the “workstation” settings, launch additional diagnostic tools, etc.
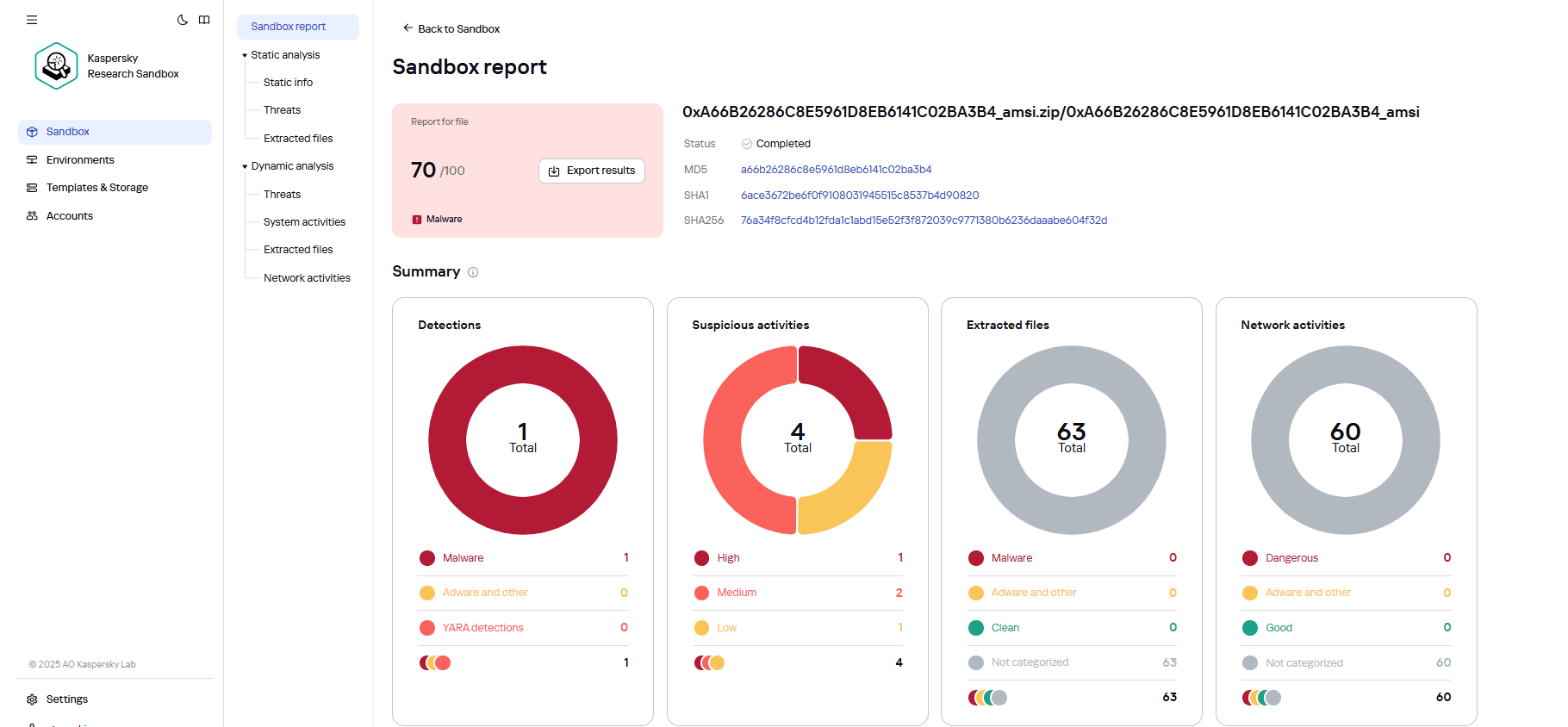
The results of the dynamic analysis can then be reviewed in a detailed report on all the malicious and suspicious activities. The report also features a map of the malware’s execution, with every dangerous step marked according to the MITRE ATT&CK international classification system.
How we reduced system requirements
A major update in this third version of our Research Sandbox is the reduction of system requirements, making it more accessible to a broader range of users. As we all know, hardware keeps getting smaller and faster over time, while software keeps getting bulkier and slower. Our Sandbox is a rare exception. So how did we achieve this?
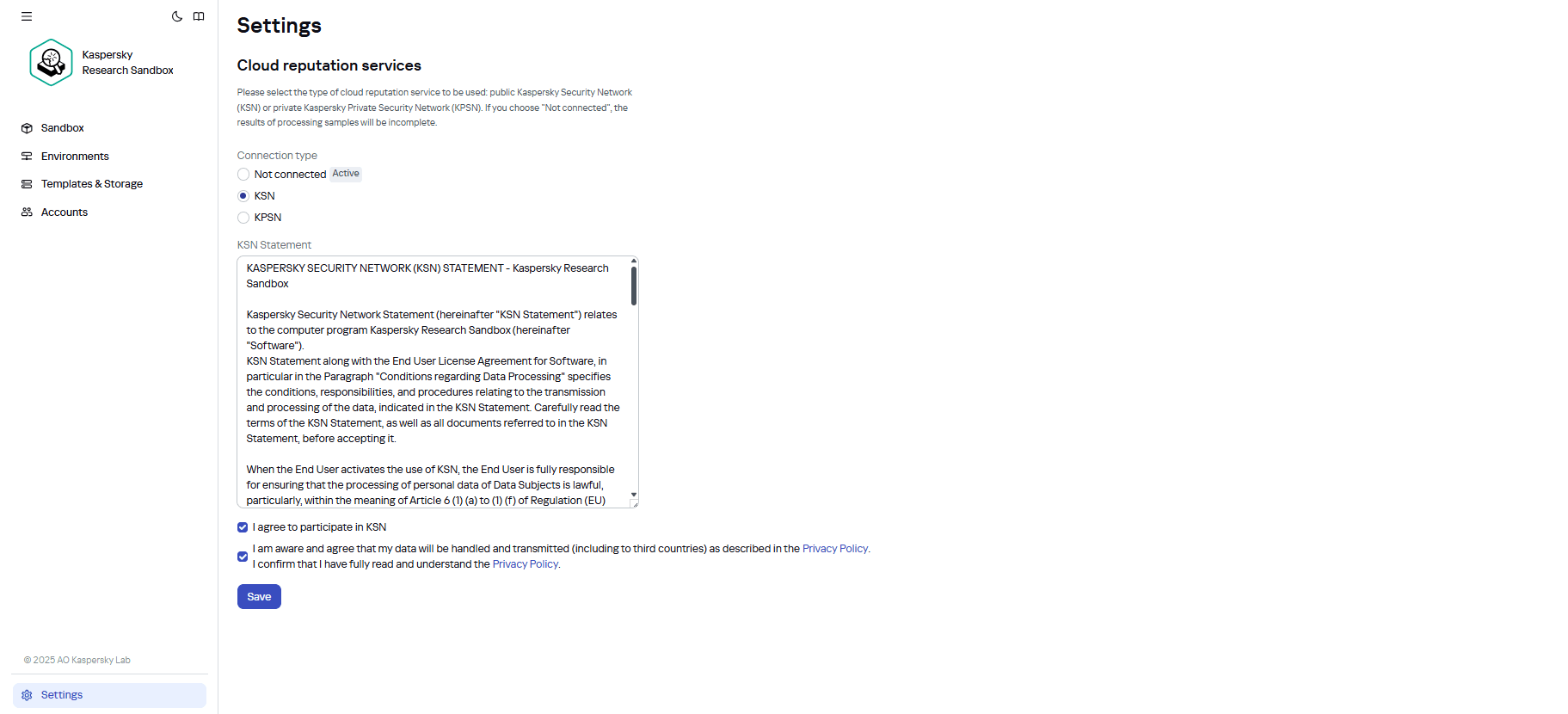
The Sandbox needs our reputation database for both dynamic and static analysis to be fully effective. Version 3.0 now allows connecting to our cloud-based KSN, meaning one less server for deployment (you need just one instead of two – effectively halving the system requirements). Of course, as previously, the user can still use an on-premise option (KPSN) that wouldn’t send anything outside and only receive updates.
Sure, there are quite a few organizations that absolutely refuse to send anything outside – not even file hashes. But even they might find this one-server option useful in reducing pilot testing costs. Then, if the Sandbox is found to meet their needs, they could then deploy a local reputation database.
The Sandbox family
Research Sandbox 3.0 is the younger sibling (one of several – there are also free and commercial cloud versions available on the open and closed Threat Intelligence Portal, respectively, and another in our KATA solution) of our internal Sandbox – the big sister that serves our antivirus lab. That’s where all the innovations are introduced, and once they’re successfully tested, they’re rolled out to the products that our clients use. We detect over 450,000 new malware samples daily – many of them with the internal Sandbox, which is a vital part of our Auto-Woodpecker.
Incidentally, the Research Sandbox is integrated with our cloud-based threat-data verification service (Threat Lookup) for analyzing URLs, hashes, and IP addresses. This service is hosted on our Threat Intelligence Portal, where the cloud Sandbox (Threat Analysis) is also located. It requires no resources or servers of its own and includes very useful additional functions for everyone ->
First and foremost, Threat Analysis can check files for attribution and similarity. This is EXTREMELY useful for investigations, incident response, and maintaining a high level of corporate network security. Attribution helps determine whether a file likely belongs to a known APT group, and instantly reveals all its known tactics and techniques, while similarity identifies similar malicious files to look for their traces in your infrastructure. Cybercriminals can modify and rebuild their tools, but they can’t hide their recognizable malicious signatures so easily.
Who’s it for?
So who’s the Research Sandbox designed for? Although it can automatically handle up to 17,000 objects per day (in the local deployment version), its primary task is to conduct in-depth analysis of specific files identified during cybersecurity incidents within an organization. To do this, there should be at least one dedicated information security specialist, or a group of specialists and a SOC (Security Operations Center). Its specialization is to thoroughly investigate, delve deeper, and analyze. It’s well-suited for antivirus analysts or incident response teams.
For some tasks, a flow-processing sandbox is needed – one that analyzes suspicious files extracted from emails and traffic; in our case – the KATA Sandbox. The Research Sandbox, on the other hand, is meant for specialists to be able to sit down, dig in, and explore connections and how things work.
This new version of the Sandbox supports the main versions of Windows (11 is in the works), Android, and Linux, as well as static analysis of executable files for other OSs like macOS. Lots of plans are in motion; the entire Sandbox family continues to evolve….
By the way, why is infosec more interesting than, say, microbiology? Well, biological bacteria and viruses don’t have intelligence; they can try to infect and even kill researchers, but they don’t plot to deceive them. And cybercriminals? They do have intelligence and they do plot all sorts of harmful shenanigans! And that’s why fighting malware is a battle of minds, which makes our field so fascinating. It’s a constant game of Sherlock vs. Moriarty – and though the stakes are high, it’s also absolutely thrilling at the same time!