March 6, 2017
StoneDrill: We’ve Found New Powerful ‘Shamoon-ish’ Wiper Malware – and It’s Serious.
If you’re a regular reader of this here blog of mine, you’ll know about our GReAT (Global Research and Analysis Team) – 40+ top-notch cybersecurity experts dotted all around the globe specializing in protecting our customers from the most sophisticated cyberthreats out there. GReATers like to compare their work to paleontology: exploring the deep web for the ‘bones’ of ‘cyber monsters’. Some may consider this an old-fashioned approach: what’s so special about analyzing the ‘bones’ of ‘creatures’ from the distant past when it’s protecting your networks from monsters that are alive now that’s key? Well, here’s a fresh story that proves that sometimes you won’t find today’s living monsters without looking at old ones…
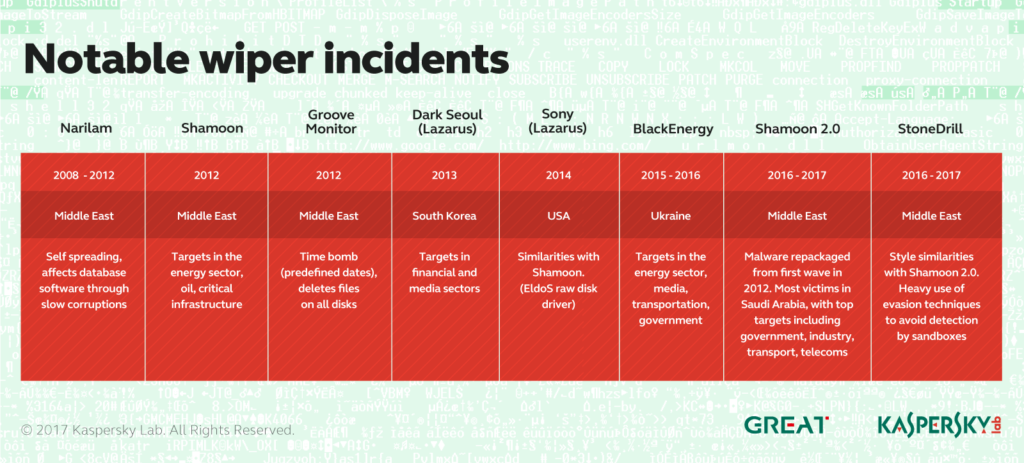
Some of you will be aware of so-called wipers – a type of malware which, once installed on an attacked PC, completely wipes all data from it – leaving the owner of the computer with a completely clean, hardly operating piece of hardware. The most famous (and infamous) wiper is Shamoon – malware which in 2012 made a lot of noise in the Middle East by destroying data on 30,000+ endpoints at the world’s largest oil company – Saudi Aramco, and also hitting another energy giant – Rasgas. Just imagine: 30,000+ pieces of inoperable hardware in the world’s largest oil company…
Curiously, since it’s devastating campaign against the Saudi company in 2012, little has been heard of Shamoon, until it returned in 2016 as Shamoon 2.0, with several new waves of attacks – again in the Middle East.
Since the new waves of Shamoon attacks began, we’ve been tuning our sensors to search for as many versions of this malware as possible (because, let’s face it, we don’t want ANY of our customers to EVER be struck by malware like Shamoon). And we managed to find several versions – hurray! But together with our haul of Shamooners, our nets unexpectedly caught a completely new type of wiper malware, which we’ve named StoneDrill.
The code base of StoneDrill is different to that of Shamoon, and that’s why we think it’s a completely new malware family; it also utilizes some advanced detection avoidance techniques, which Shamoon doesn’t. So it’s a new player, for sure. And one of the most unusual – and worrying – things we’ve learned about this malware is that, unlike Shamoon, StoneDrill doesn’t limit the scope of its targets to Saudi Arabia or other neighboring countries. We’ve found only two targets of this malware so far, and one of them is based in Europe.
Why is this worrying? Because this finding indicates that certain malicious actors armed with devastating cyber-tools are testing the water in regions in which previously actors of this type were rarely interested.
So, my advice to companies in Europe who could be of interest to the operators behind StoneDrill, or maybe even Shamoon: prepare your defenses for this type of threat against your network. It’s not something only oil-and-gas companies in the Middle East can be affected by anymore. It seems to be going global.
Back to cyber-paleontology…
I mentioned earlier that we unexpectedly found StoneDrill while looking for Shamoon samples. Sure, it was unexpected – but it wasn’t accidental…
In order to find new or similar variants of known malware, our researchers (among other tools) use YARA rules. These make up a specific tool that allows to set multiple different search parameters and filter our malware databases through these rules.
Translating into a human language the process of hunting malware with YARA rules is like searching for a particular face in a crowd without knowing that face. Imagine you have a pen-pal. After years of letters emails between you, you decide to meet up – in a crowded train station. But, since you both decided never to send a photo to the other (“let’s not send pics of ourselves – for fun/intrigue!”), you don’t know what your pen-pal looks like; the only things you know are a few details like age, height, body composition, hair color, eye color, and maybe the type of clothes they normally wear. So, in that crowded station, you may come across someone who matches all the physical traits of your pen-pal, but you’ll not know if it really is them until you start talking to them.
Well, pretty much the same thing happened with StoneDrill.
Our researchers identified some unique parameters of the latest versions of Shamoon. Based on these parameters our guys created some YARA rules, hit the search button, and then started analyzing the catch. Subsequently they found a sample that matched Shamoon’s parameters; however, after a closer look it became clear that the newly found malware wasn’t Shamoon at all, but from a completely new family of wiper malware.
Back to our example with the pen-pals, this would mean that you’d identify someone else who had parameters that match your pen-pal’s, but it isn’t your pen-pal. Maybe it’s a relative of your pen-pal, who knows?
Why am I explaining this here?
Well, remember the paleontology metaphor at the beginning of this post? This is what I meant when I wrote that sometimes it’s impossible to catch new monsters without knowing all about old ones. See, it is worthwhile ).
But there’s another reason why I want to talk about how we caught StoneDrill.
The fact that we identified StoneDrill while looking for Shamoon means that both are built and operate in pretty much the same ‘style’, even though their code is completely different. When I say ‘style’ I’m referring to certain approaches how the malware would operate, hide itself from both security software and researchers, and so on. It’s not the kind of similarity you’d find between, say, two brothers, but one you’d find between two students of the same teacher. Or between two members of the same pen-pals’ club, if you prefer.
In other words, the similarities between Shamoon and StoneDrill are most likely not a coincidence. Were Shamoon and StoneDrill written by one and the same author(s)? Is StoneDrill a specific tool of Shamoon’s operators? Or are these two different beasts of two completely different actors who might have attended the same malware writing schools? We don’t know. Anything is possible; meanwhile, we’re still investigating, and will be presenting our findings at the upcoming SAS conference.
But wait! That’s not all!…
When our GReAT guys were digging into the code of StoneDrill, they started experiencing some serious déjà vu: they’d seen some of those lines of code before! Where? In another cyber-espionage operation called Newsbeef – on which we published a blogpost last year. So here’s another variable in this equation: Newsbeef. Is StoneDrill a tool used by Newsbeef’s operators for data-wiping purposes? Again, this is still an unanswered question.
Now, if we were geopolitical experts or armchair philosophers we’d most likely make some assumptions regarding these connections. As Winnie the Pooh once said: “That buzzing noise means something”.
But (luckily!) we aren’t geopolitical experts or armchair philosophers. We’re doing the tough job of saving the world from all cyberthreats regardless of their origin or purpose. The only reason I mention connections between Shamoon, StoneDrill and Newsbeef here is because we found them. And from my perspective this is a good illustration of the usefulness of professional threat intelligence for your company or a government organization seeking a better understanding of what’s going on around it. It helps to get an understanding things. And when you understand things, you can better prepare against the risks these things may bring.
So stay tuned, read the detailed findings of our researchers at Securelist, and if you’re interested in getting more professional threat intelligence, don’t hesitate to subscribe to our APT intelligence reporting service.
Now I’m passing the mic to the authors of the StoneDrill discovery: detailed technical analysis can be found here.
PS:
If you want your security team to be able to analyze malware just as deeply and professionally as GReAT do, send them to our training sessions. The earliest one will take place at the SAS-2017 conference in the beginning of April; this year we’re having it in Sint-Maarten, because we learned long ago that the Caribbean is the perfect place for hardcore cybersecurity discussions and training. Book everything here – and pack your bags (inc. swimsuit)!
.@kaspersky reveals a massive #cyberwar operation that involves at least three wiper-style malwareTweet