December 6, 2016
A Brief History of DDoS Attacks.
And so it’s come to pass: the abbreviation ‘DDoS‘ has entered the lexicon to such an extent that it often doesn’t get written out in full these days in the general interest newspapers. Well, some actually may still not know what it stands for, but everyone and their dog does know that a DDoS is very bad thing for a certain large target, with something very important suddenly not working, with employees twiddling their thumbs as the network’s down, and with their tech-support’s telephones requiring an ice bath as they’re so hot from ringing – and disgruntled clients swearing down them all the time. What’s more, everyone and their cat also knows that normally a DDoS attack gets carried out by unknown, mysterious – and just plain bad – cyber-enemies.
DDoS attacks have evolved very quickly, as you’ll find out reading this blogpost. They’ve grown much nastier and become a lot more technically advanced; from time to time the adopt utterly unusual attack methods; they go after fresh new targets; and break new world records in being the biggest and baddest DDoS’s ever. But, then, the world in which DDoS find themselves in has evolved very quickly too. Everything and the kitchen sink is online: the number of assorted ‘smart’ [sic] devices connected to the net now far outstrips the number of good old desktop and laptop computers.
The result of these two evolutions running in parallel – of DDoS’s themselves plus the digital landscape in which they dwell – has brought us equally evolved headlines: botnets made up of IP cameras and home Wi-Fi routers breaking DDoS records on size (Mirai), and massive DDoS attacks on Russian banks.
If, earlier, botnets were made up of zombie PCs, soon they’ll be made up of zombie refrigerators, vacuum cleaners, tumble dryers and coffee machines.
So what’s next?
Nothing good, that’s for sure. In the past it always ended badly for the victims involved. But how badly might victims suffer in the future? To make a best guess at that we need to look to the past; then we’ll have a better idea of what may be in store for the future. Therefore, herewith, a brief run-through of the history of DDoS attacks, for your reading and historically enlightening pleasure.
What follows is my subjective Top-8 DDoS attacks of all time. ‘Top’ not as in ‘great’, but as in ‘worst’, if you see what I mean. All eight caused serious outages either of a big chunk of the Internet or a large Internet service.
Before I start – a caveat: not all eight are fully ‘DDoS attacks’ as per today’s understanding of the word; however, the ‘distributed’ element was present in all eight, as was their causing major network disruption.
1. The Morris worm (1988)
 Robert Tappan Morris – creator of the first computer worm on the Internet
Robert Tappan Morris – creator of the first computer worm on the Internet
While still a grad student, Robert Tappan Morris developed his worm purely for research purposes (“to gauge the size of the Internet”). However, as ever, hidden in the code was a mistake, as a result of which the worm couldn’t determine whether a system was ‘clean’ or infected (by itself!). Instead of a one-off attack on remote computers, the worm copied itself on one and the same system over and over. And over and over. And over and over…….. As a result the network crashed – all 60,000 nodes of the network. The infected ARPANET – an early prototype for the Internet – DDos’ed itself!
Morris pleaded guilty, repented, and was given 400 hours’ community service and a fine of $10,000.
2. Melissa (1999)
 David Smith, creator of Melissa, the mass-mailing virus that left Microsoft and Intel without email
David Smith, creator of Melissa, the mass-mailing virus that left Microsoft and Intel without email
A simple mail macro-virus which affected MS Office documents. If a user opened a file, the virus emailed itself to 50 recipients from the address book of the victim.
So, er, where’s the DDoS connection, you may be asking….
Well, those 50 emails sent from each victim caused nothing less than a gigantically grandiose epidemic, which snowballed out of control: the distributed attack spread right round the globe. It didn’t take aim at one particular target – sort of; it targeted the whole global system of email instead! The macro managed to increase world mail traffic considerably, and forced many companies to simply disable their email servers.
This virus writer was also caught, tried and prosecuted.
3. The DDoS Attack on Amazon, eBay, Dell, CNN and More (2000)
This DDoS is perhaps most striking in that, though it caused immense damage, the guy behind it was hardly punished at all.
This is what happened: a 15-year-old hacker who went by the name MafiaBoy brought down nearly all the main Internet portals, including Yahoo!, then the world’s top search engine (Google was still in diapers). The financial damaged caused by MafiaBoy was estimated at 1.2 billion dollars.
The reason why he did what he did was fairly typical for the times: he just wanted to show the cyberworld how cool he was. He wasn’t interested in money one bit. It was all just adolescent ego – aided and abetted by the inherent vulnerability of the Internet.
Due to his still being a minor, a Canadian court sentenced him to just eight months in a juvenile detention center.
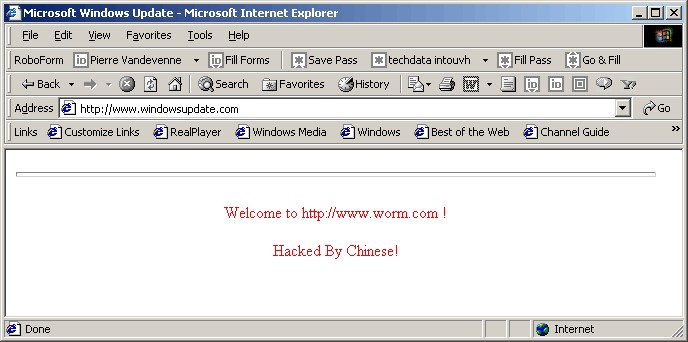
4. Code Red (2001)
Here’s another that came before the era of cybercrime as we know it today; as such – it wasn’t after money. It was simply maliciousness for the silly sake of it.
Code Red attacked computers running Microsoft’s IIS web server. It left messages saying ‘Hacked by Chinese’, and even brought down the White House’s site.
The worm did three things:
a) It substituted the useful content of a page with the following sacramental phrase:
b) It distributed itself across new web servers;
c) It carried out DDoS attacks on a pre-defined set of web addresses – including that of the White House, which it brought down at a similarly pre-defined time, as per the corresponding entry in the code.
It’s reckoned that it managed to affect more than a million (!) web servers all around the world, i.e., a considerable proportion of the whole of the Internet. It lived only in the memory of the victim’s computer, creating no files.
Who wrote Code Red and why it was released still remains a mystery.
What was particularly interesting about Code Red was that the vulnerability in the web server that was exploited by the worm had been patched by Microsoft a full month before the outbreak. The take away: never delay with your updates, folks!
5. SQL Slammer (2003)
This was a small tiny but VERY nasty bit of maliciousness – in all just 376 bytes (no typos folks – no ‘kilo’, or ‘mega’, or ‘giga’ missing). In January 2003 it managed to infect hundreds of thousands of servers all over the world in 15 minutes, increase global traffic by 25%, and leave South Korea with neither Internet nor mobile telecoms (!) for several hours, having DDoS’ed the country to smithereens. Moreover, the hole in Microsoft SQL Server 2000 that it exploited had been patched – not a month before like with Code Red – but six months earlier!
There turned out to be a great many systems full of holes back then and the computer world took a serious hit. On that fateful Saturday morning none other than our (now) top expert Aleks Gostev, who’d only been with us at KL a month, was alone on the weekend shift. I remember his ‘christening’ into the world of premier-league maliciousness detection well and will never forget it!
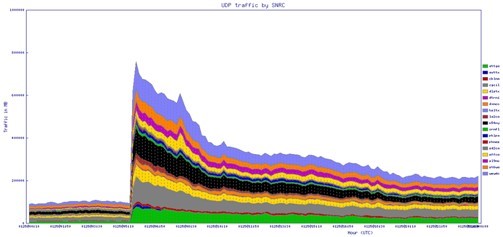 The jump in traffic looked something like this
The jump in traffic looked something like this
Among other things this epidemic disrupted 13,000 Bank of America ATMs and, by all accounts, it actively (albeit indirectly) led to 50 million folks in northwestern USA going without electricity in August 2003.
6. Estonia (2006)
In 2007 the government of Estonia decided to move the Bronze Soldier of Tallinn, built at the site of several war graves, from the center of the capital to the nearby Tallinn Military Cemetery. The statue is a memorial to Soviet soldiers who fell in World War II while fighting with Nazi troops. Estonia’s Russian-speaking community objected strongly to the move, but it still went ahead, causing two nights of riots and mass arrests. That’s the brief background.
Around the time the monument was moved a historic DDoS was launched on various Estonian organizations. It wasn’t the biggest DDoS in history, but it was the first time criminal spammer botnets threatened the national security of a country: the Estonian section of the Internet was practically completely crashed. Banks, Internet providers, newspapers, government sites… all of it brought to a standstill. Rumors have it that the Russian state was behind it, but we couldn’t confirm that. We only know that criminal botnets were used, as well as overly enthusiastic individuals.
The main lesson from the attack on Estonia: cybercrime had become a possible threat to national and international security, and that the digital world that we’d built turned out to be extremely vulnerable.
7. DDoS in Southern Russia (2007)
This is a much less well-known DDoS, but no less important for it. In the hot summer of 2007 in the Krasnodar region in southern Russia, the cities of Adygea and Astrakhan had only intermittent Internet coverage – it went off, came back on again, over and over. Turned out that the reason was a DDoS that had taken down the largest net provider in the region.
Naturally there was panic, with engineers running round in circles, routers – and brains – smoking, swearing, clients – including the VIP ones – starting to ask when the Internet will come be back on, and law enforcement wondering just who they were meant to be arresting – and for what!
The attacks came in waves for a whole month, reaching a staggering (for 2007) 10 gigabytes per second. The attacks were also very unusual: they used botnets, but made more use of file exchanging peer sites, which was unprecedented back then outside research projects. Who was behind the attacks was never discovered.
This DDoS was a pivotal moment for Russia. The whole Internet for a whole region was being switched on and off like a torch and there was nothing anyone could do about it. Before this incident no one took any notice of DDoS threats; afterwards – just the opposite: they were treated as acute current threats to be taken seriously. Technologies appeared, and telecoms companies started to actively install new specialized kit. We did our bit too – developing our own solution.
8. Political DDoS in Russia (2011-2012)
Between December 2011 and March 2012 there was plenty of political tension in Russia: both the Duma (parliament) and Presidential elections were taking place, and they were accompanied by lots of political demonstrations. To top it all off there was a shoot-out between opposing DDoS forces. Both opposition and pro-government sites were DDoSed. The main take-away: this was the first time in Russia cybercriminal methods were so widely and blatantly applied for political ends.
What Does the Future Hold?
DDoS’es didn’t stop in 2012. Actually, just the opposite: a whole, fully-commercial criminal DDoS industry has grown up. The motivation for this is clear: money, cybercrime as a service, choking up services to order. Hacktivists are in on the DDoS thing too, as are cyber-generals the world over.
Today it’s hard to imagine an epidemic like Slammer (but now with so many ‘smart’ devices connected to the Internet and exchanging data, anything could happen). But the bad guys aren’t giving up, and recent DDoS’es on the Internet of Things prove this. Our dependence on the Internet and smart kit is growing, and so does the potential for damage from any crash or complete outage, including man-made ones.
For now the world has stuck – a little in the dark past, a little in the dangerous future. And between the two – an alarming present. There are still reasons to be optimistic; however, I fear that we’ll still see quite a few unpleasant DDoS attacks yet.