July 2, 2013
Emulate to exterminate.
First, a bit of rewind/intro…:
100% guaranteed protection doesn’t exist. You probably know that perfectly well by now. Indeed, even the most reliable antivirus sometimes gets bypassed in professional attacks. That’s bad news enough already. What’s even worse news is that inferior antiviruses get bypassed a lot more frequently.
If they want, highly professional criminals can hack into anything; thankfully, such cyber-Moriatys are few and far between. For the most part, cyber-outrages are carried out by common-or-garden programmers who seem to get their right and wrong all mixed up – seduced by greed and thinking they can get away with it (ha!). These chancers usually don’t have sufficient criminal cyber-skills to pull off hacking the most advanced mega-defenses out there, but they are more than capable of getting into computers that are either not protected at all or which have colander-protection installed. And, alas, such comps in the world are twenty a penny.
The basic logic of it all is rather straightforward:
The stronger the protection – the stronger the defenses, obviously. At the same time, the more professional the attack – the stronger the defenses it can break.
Now, with 2.5 billion Internet users potential victims out there, this logic leads to the following economics:
Criminals don’t need to go to all the bother of coming up with super-mega skeleton keys for breaking into super-mega secure vaults (especially when what is often saved in such super-mega secure vaults can be some real creepy/weird/dangerous stuff it’s best not to know about). It’s much simpler – cheaper – to break into something more down-to-earth, like a neighbor’s network, since their defenses are bound to be much, much lighter, and their stashes more realizable.
So you get the picture: for the average hacker, there’s no point going to the trouble of preparing for and carrying out mega-professional attacks. Nor is there much sense in switching their criminal focus from Windows to Mac. It’s much more effective to ‘carpet-bomb’ – affecting as many victims as possible with non-pinpointed attacks that don’t take a lot of hassle or brains to carry out.
The better the protection – the less interesting it is for the bad guys. They won’t bother going to the trouble of breaking it, they’ll just find other – more vulnerable – victims elsewhere.
Now, let me tell you more about a feature that puts cybercrims off attacking particularly your comp, and has them decide to go elsewhere where the feature doesn’t reside. Yep, it’s time for another eye-opening excursion under the hood of our antivirus and to let you know more about how the letter K in your taskbar makes you a big turn-off to the cyber-trespassers – through protection from future threats with emulation.
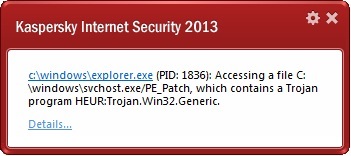
I wrote ‘more‘ above as I’ve already talked about our emulation on these here cyberpages before. For those who might not have read that – I suggest a quick read. For the busy bees among you, below – a quick synopsis…
Briefly, emulation is a method for automatically detecting brand new malware – by analyzing the behavior of suspicious programs without actually running them – so that they can’t cause harm to the computer. But how can we analyze a program without launching it? Well that’s just what emulation is all about. It emulates the running of a program – without actually running it. The emulator creates a special virtual environment in which the program is run. It’s a bit like testing/analyzing a (human) bodily virus (e.g., a strain of flu) in a test tube, as opposed to testing/analyzing it while it runs through the veins of some poor soul who’s been struck down by influenza. It’s much less harmful doing it that way – to the stricken individual in general, or to the computer in general – i.e., to the environment of the host.
With emulation, I’m happy to report, maliciousness has nowhere to hide! Well, almost… There is just one big ‘but’ spoiling things:
The most resourcefully crafty (and most dangerous) malicious programs have learned how to recognize artificial test tube environments they may find themselves in, and automatically change their attack vectors for as long as they can’t find a weak point in the defenses.
We’re talking here special anti-emulator tricks.
Examples: launching undocumented functions, checking the authenticity of the environment by tracking changes to the processor register, analysis of error codes, searching for specified code in the memory, use of ‘logic bombs’ to put the emulator into infinite cycles, and so on and so forth.
As soon as a trick works, the maliciousness understands that it’s inside a test tube, and quickly transforms itself into a seemingly benign program in whose mouth the proverbial butter wouldn’t melt, or simply shuts itself down. Then, in the background, on the sly, it tries to attack using different logic in its ongoing attempts to unnoticeably slip past the emulator.
Many years of battle on this front followed the classic toing-and-froing scenario of old school trench-to-trench combat – sides taking it in turns in getting the upper hand over their opponent, thinking up new cunningness and counter-cunningness on and on, all of it bringing little mirth to the average user. Because of how lengthy and wearisome the battle has been and how many resources it has consumed, some experts decided that emulation’s days as a useful antimalware technology were numbered. We nevertheless managed to find a way to have the last laugh in the matter :).
Clearly what was needed to win with emulation was to be able to create a test tube (testing environment) that was identical to the human body (actual computer environment).
Well, I’m not sure about biological viruses in the era of cloning :), but as regards computer malice it is theoretically possible; however, it’s incredibly expensive and reeaally difficult to put into practice. Why? Basically because a whole new operating system needs to be developed – one that would correspond to the original. And such an operating system would have to be launched for each and every suspicious file. Just imagine how many system resources that operation would require!
So we went another route – a road less not traveled – a by-pass…
Now, the vast majority of malicious programs operate at the user level of the OS. However, for system calls (for example, file reading/writing), they interact with the kernel of the system at the system level. Between these two levels there’s one big difference: at the user level programs can see changes made to the environment (and consequently use anti-emulator tricks), while at the system level – they can’t.
Thus, we’ve concentrated all our sophisticated antimalware emulation tricks at the system level, while at the user level we focus on achieving the very highest possible ratio of similarity to the original environment. The result: a near-perfect solution for making the ‘test tube’ invisible!
Specifically, we correctly emulate the execution of all API-function calls and then move to the system level for the deep antimalware analysis. Accordingly, malice at the user level gets a nice feeling of impunity in a virgin environment – actually a false sense of impunity – and, at last, gives away its malicious essence and intent. Bingo!
Alas, as with any technology, our turbo-charged (and, incidentally, super-stable) emulator slows computer performance quite a bit, so we’ve added an intelligent hardware accelerator to it, which selectively bypasses software-based emulation and executes some bits of a program on a real processor. I won’t go into the details (the patent application is still pending!), but I will just say that what we’ve come up with is a duet of technologies that works much quicker than traditional emulation! Bingo again!


